Difference between revisions of "Template:AWSinstructions"
| (One intermediate revision by the same user not shown) | |||
| Line 1: | Line 1: | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
== '''Setup your AWS account and Permissions''' == | == '''Setup your AWS account and Permissions''' == | ||
Refer to the online AWS documentation at Set up your AWS Account. Follow the steps outlined in the sections below to create your account and a user and get started:<br> | Refer to the online AWS documentation at Set up your AWS Account. Follow the steps outlined in the sections below to create your account and a user and get started:<br> | ||
| − | * [https://docs.aws.amazon.com/iot/latest/developerguide/setting-up.html#aws-registration Sign up for an AWS account] | + | * [https://docs.aws.amazon.com/iot/latest/developerguide/setting-up.html#aws-registration Sign up for an AWS account and] |
* [https://docs.aws.amazon.com/iot/latest/developerguide/setting-up.html#create-iam-user Create a user and grant permissions] | * [https://docs.aws.amazon.com/iot/latest/developerguide/setting-up.html#create-iam-user Create a user and grant permissions] | ||
* [https://docs.aws.amazon.com/iot/latest/developerguide/setting-up.html#iot-console-signin Open the AWS IoT console] | * [https://docs.aws.amazon.com/iot/latest/developerguide/setting-up.html#iot-console-signin Open the AWS IoT console] | ||
<br> | <br> | ||
| − | + | NOTE – The examples in this document are intended only for dev environments. All devices in your production fleet must have credentials with privileges that authorize only intended actions on specific resources. The specific permission policies can vary for your use case. Identify the permission policies that best meet your business and security requirements. For more information, refer to [https://docs.aws.amazon.com/iot/latest/developerguide/example-iot-policies.html Example policies] and [https://docs.aws.amazon.com/iot/latest/developerguide/security-best-practices.html Security Best practices]. | |
<br> | <br> | ||
| − | |||
== '''Create Resources in AWS IoT''' == | == '''Create Resources in AWS IoT''' == | ||
Refer to the online AWS documentation at Create AWS IoT Resources. Follow the steps outlined in these sections to provision resources for your device: | Refer to the online AWS documentation at Create AWS IoT Resources. Follow the steps outlined in these sections to provision resources for your device: | ||
| Line 31: | Line 14: | ||
* [https://docs.aws.amazon.com/iot/latest/developerguide/create-iot-resources.html#create-aws-thing Create a thing object] | * [https://docs.aws.amazon.com/iot/latest/developerguide/create-iot-resources.html#create-aws-thing Create a thing object] | ||
<br> | <br> | ||
| − | + | NOTE – The examples in this document are intended only for dev environments. All devices in your production fleet must have credentials with privileges that authorize only intended actions on specific resources. The specific permission policies can vary for your use case. Identify the permission policies that best meet your business and security requirements. For more information, refer to [https://docs.aws.amazon.com/iot/latest/developerguide/example-iot-policies.html Example policies] and [https://docs.aws.amazon.com/iot/latest/developerguide/security-best-practices.html Security Best practices]. | |
<br> | <br> | ||
| − | == ''' | + | == '''Provision the Device with credentials''' == |
Whole device, AWS IoT and testing information can be downloaded in PDF format [https://wiki.teltonika-gps.com/images/c/c5/MQTT_AWS_IoT_Custom_Configuration_Guide_V1.pdf here.] | Whole device, AWS IoT and testing information can be downloaded in PDF format [https://wiki.teltonika-gps.com/images/c/c5/MQTT_AWS_IoT_Custom_Configuration_Guide_V1.pdf here.] | ||
| − | + | === ''AWS IoT Core Configuration'' === | |
| − | === | + | ==== ''Setting up AWS IoT Core'' ==== |
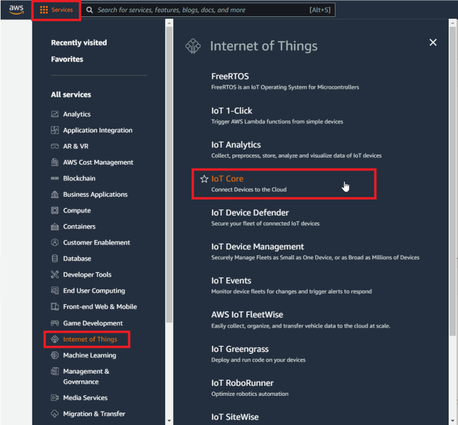
| − | ==== | + | When logged in the AWS console, click on Services on the top left hand side screen, to access IoT core. |
| − | + | <br> | |
| − | + | [[File:AWS_MQTT_1.png|frameless|alt=|center|934x425px]] | |
| − | |||
| − | |||
| − | |||
| − | [[File: | ||
<div style="text-align: center;">Figure 1. Accessing AWS IoT core from AWS console</div> | <div style="text-align: center;">Figure 1. Accessing AWS IoT core from AWS console</div> | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
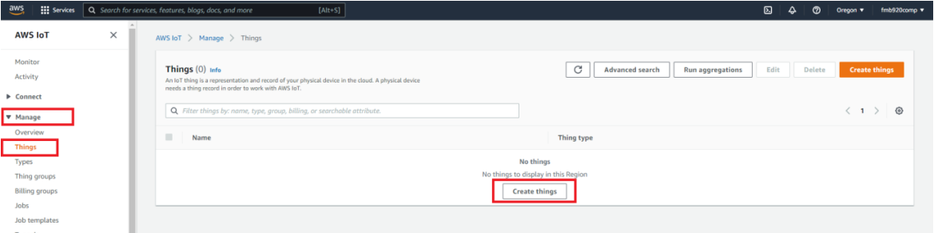
| − | + | After accessing AWS IoT core, select Manage on the sidebar on the left side, then select Things (Manage- >Things). And click on Create things. | |
<br> | <br> | ||
| − | [[File: | + | [[File:AWS_MQTT_2.png|frameless|alt=|center|934x425px]] |
| − | <div style="text-align: center;">Figure | + | <div style="text-align: center;">Figure 2. Accessing Things</div> |
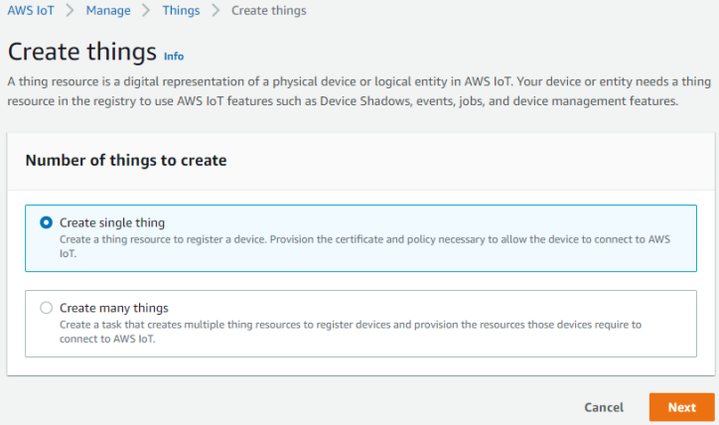
| − | + | Afterwards for select Create single thing and click Next. | |
| − | |||
| − | Afterwards select Create single thing and click Next. | ||
<br> | <br> | ||
| − | [[File: | + | [[File:AWS_MQTT_3.png|frameless|alt=|center|934x425px]] |
| − | <div style="text-align: center;">Figure 5. Creating | + | <div style="text-align: center;">Figure 3. Creating single thing</div> |
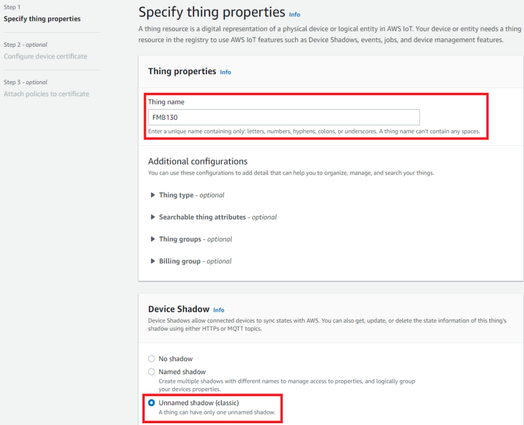
| + | After creating single thing, enter Thing’s name and in the Device Shadow tab select Unnamed shadow (classic). Then click Next. | ||
| + | [[File:AWS_MQTT_4.png|frameless|alt=|center|934x425px]] | ||
| + | <div style="text-align: center;">Figure 4. Specifying thing properties</div> | ||
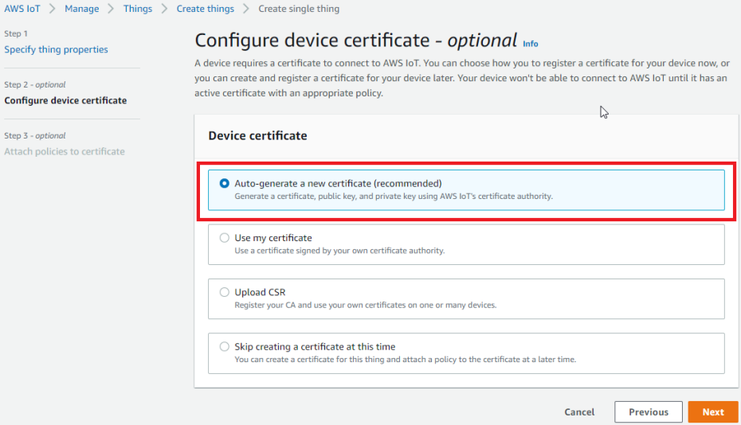
| + | Then when selecting Device certificate, select Auto-generate a new certificate and click Next | ||
| + | [[File:AWS_MQTT_5.png|frameless|alt=|center|934x425px]] | ||
| + | <div style="text-align: center;">Figure 5. Selecting Certificate</div> | ||
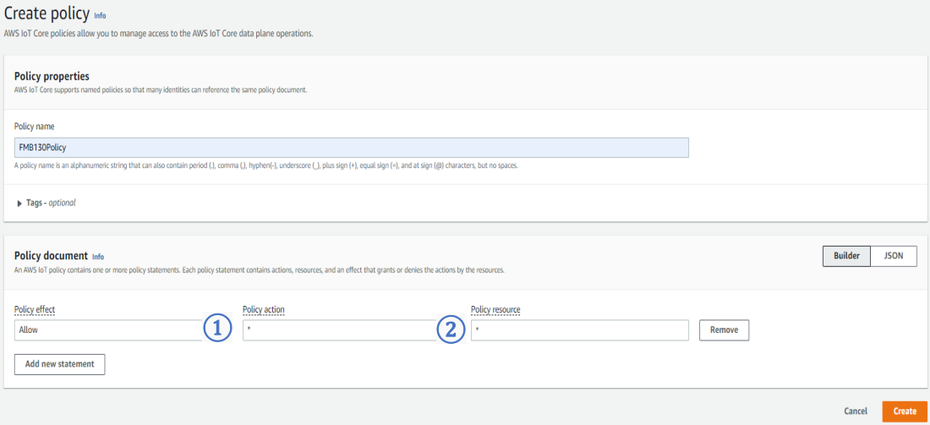
| + | After this select Create policy to create it and attach it to Certificate. In the Create Policy window, enter Policy name. In the Policy document (1) tab for Policy Action (2) select * and for Policy resource enter * . | ||
| + | [[File:AWS_MQTT_6.png|frameless|alt=|center|934x425px]] | ||
| + | <div style="text-align: center;">Figure 6. Creating policy for Certificate</div> | ||
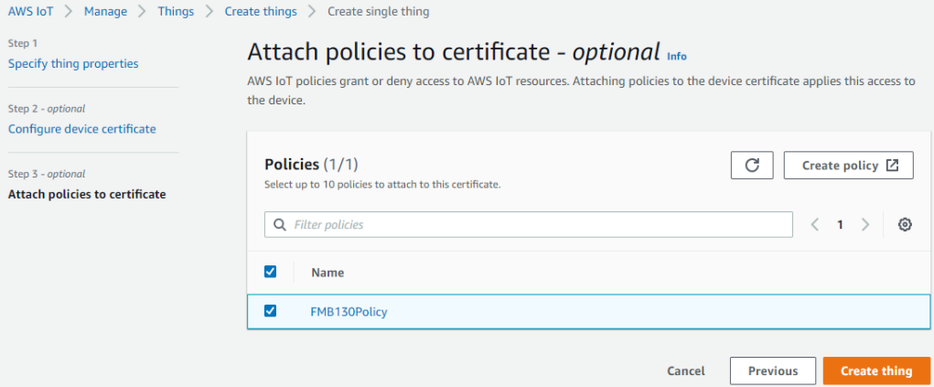
| + | After creating policy, return to Certificate tab (Seperate tab after pressing Create policy should‘ve popped out). Then select the created policy to attach it to the certificate and thing. After that click Create thing | ||
| + | [[File:AWS_MQTT_7.png|frameless|alt=|center|934x425px]] | ||
| + | <div style="text-align: center;">Figure 7. Attaching created certificate and creating thing</div> | ||
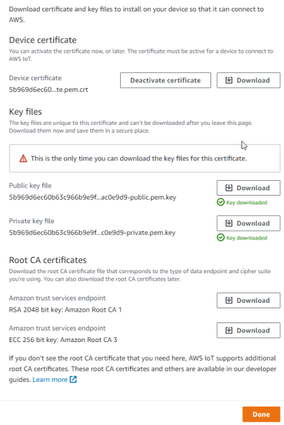
| + | Then window with Certificate files and key files download options should pop out. It‘s recommended to download all files, because later some of them will not be available for download. The files that are required for usage with FMX devices are: Device certificate (1), private key(2), and Amazon Root CA 1 file(3), but it‘s recommended to download them all and store them in secured place. | ||
| + | [[File:AWS_MQTT_8.png|frameless|alt=|center|934x425px]] | ||
| + | <div style="text-align: center;">Figure 8. Certificate files download window</div> | ||
| − | + | ==== ''Finding device data endpoint (server domain)'' ==== | |
| − | + | To receive server domain (in AWS endpoint) click on the side bar on the left Settings. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | ==== | ||
| − | To receive server domain (in AWS endpoint) click on the side bar on the left Settings | ||
Or click on the side bar on left side Things, select the created thing, after it click Interact->View Settings. Whole path - (Things->*YourThingName*->Interact->ViewSettings). Page containing endpoint will open. Copy the whole endpoint address. | Or click on the side bar on left side Things, select the created thing, after it click Interact->View Settings. Whole path - (Things->*YourThingName*->Interact->ViewSettings). Page containing endpoint will open. Copy the whole endpoint address. | ||
| − | Port for accessing this endpoint is 8883. | + | Port for accessing this endpoint is 8883. |
| − | [[File: | + | [[File:AWS_MQTT_9.png|frameless|alt=|center|934x425px]] |
| − | <div style="text-align: center;">Figure | + | <div style="text-align: center;">Figure 9. Device data endpoint</div> |
| − | === | + | === ''Configuring the device'' === |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | ==== ''Security and certificates'' ==== | |
| − | [[File: | + | Find Certificate file ending with extension pem.crt Private key file and AmazoonRootCA1 file (no need to change filenames). These file should have been downloaded when creating Thing in AWS IoT Core. |
| − | <div style="text-align: center;">Figure | + | [[File:AWS_MQTT_10.png|frameless|alt=|center|934x425px]] |
| + | <div style="text-align: center;">Figure 10. Certificate files</div> | ||
| + | Upload the mentioned files in the Security tab in the Teltonika Configurator. | ||
| + | [[File:AWS_MQTT_11.png|frameless|alt=|center|934x425px]] | ||
| + | <div style="text-align: center;">Figure 11. Uploading certificates</div> | ||
| + | After uploading certificates, go to System tab and in Data protocol section select - Codec JSON. | ||
| − | + | [[File:AWS_MQTT_12.png|frameless|alt=|center|934x425px]] | |
| − | [[File: | + | <div style="text-align: center;">Figure 12. Selecting Data Protocol</div> |
| − | <div style="text-align: center;">Figure | ||
| − | ==== | + | ==== ''Device GPRS configuration for AWS IoT Custom MQTT settings'' ==== |
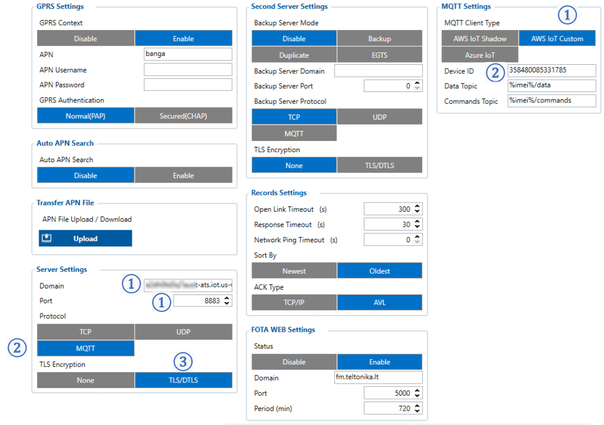
In the GPRS tab, under Server Settings select: | In the GPRS tab, under Server Settings select: | ||
# Domain – Endpoint from the AWS, Port: 8883 | # Domain – Endpoint from the AWS, Port: 8883 | ||
# Protocol – MQTT | # Protocol – MQTT | ||
# TLS Encryption – TLS/DTLS | # TLS Encryption – TLS/DTLS | ||
| − | + | <br> | |
In the MQTT Settings section select: | In the MQTT Settings section select: | ||
# MQTT Client Type – AWS IoT Custom | # MQTT Client Type – AWS IoT Custom | ||
# Device ID – enter device IMEI (optional) | # Device ID – enter device IMEI (optional) | ||
# Leave Data and Command Topics unchanged. | # Leave Data and Command Topics unchanged. | ||
| − | + | <br> | |
Save the configuration to the device. | Save the configuration to the device. | ||
| − | [[File: | + | [[File:AWS_MQTT_13.png|frameless|alt=|center|934x425px]] |
| − | <div style="text-align: center;">Figure | + | <div style="text-align: center;">Figure 13. GPRS Settings for MQTT AWS IoT Custom</div> |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| + | == '''Run the demo'''== | ||
| + | The data received from the device can be found in the MQTT test client, which can be found in the bottom of sidebar on the left. | ||
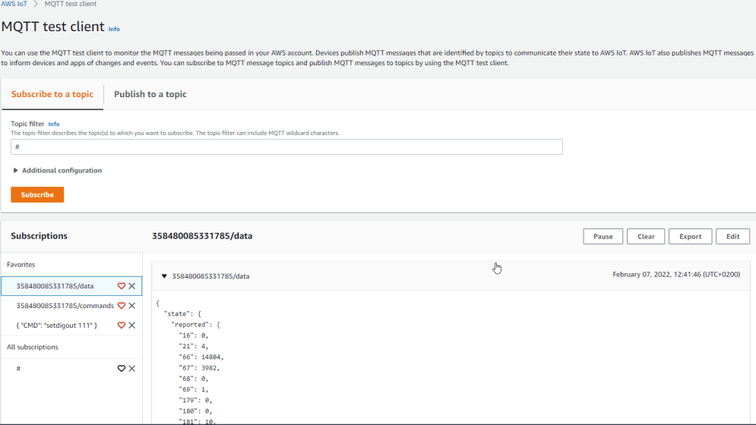
To see incoming data, subscribe to topic - *DeviceImei*/data . Or subscribe to # to see all incoming outgoing data in the Topics. | To see incoming data, subscribe to topic - *DeviceImei*/data . Or subscribe to # to see all incoming outgoing data in the Topics. | ||
| − | [[File: | + | [[File:AWS_MQTT_14.png|frameless|alt=|center|934x425px]] |
| − | <div style="text-align: center;">Figure | + | <div style="text-align: center;">Figure 14. Subscribing to data topic</div> |
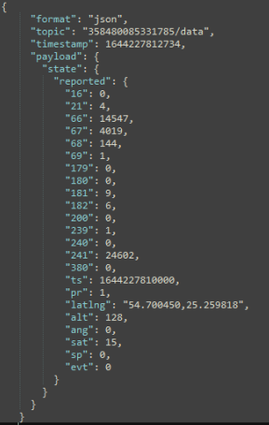
| − | + | Incoming data is received in JSON format, for e.g.: | |
| − | |||
| − | Incoming data is received in JSON format, for e.g.: | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| + | [[File:AWS_MQTT_15.png|frameless|alt=|center|934x425px]] | ||
| + | <div style="text-align: center;">Figure 15. Received data format</div> | ||
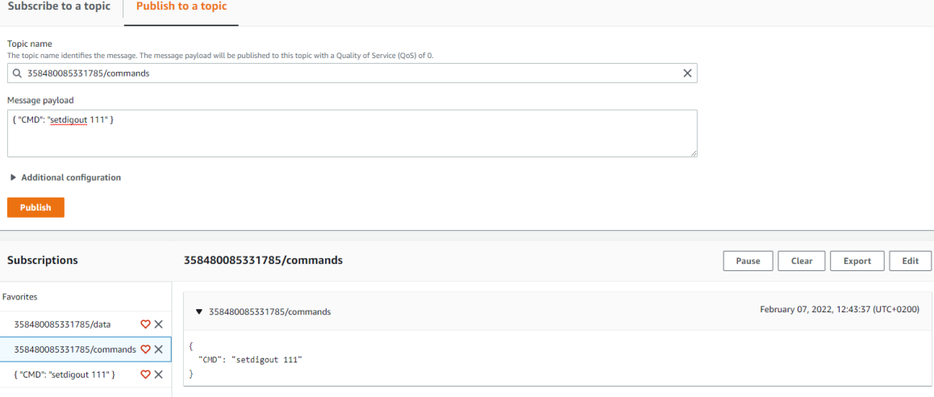
| + | To send SMS/GPRS commands to the device, in the same MQTT test client window select Publish to a topic. Enter topic name - *DeviceIMEI*/commands . In the Message payload enter wanted GPRS/SMS command in following format and press Publish: | ||
| + | [[File:AWS_MQTT_16.png|frameless|alt=|center|934x425px]] | ||
| + | <div style="text-align: center;">Figure 16. Sending Command in AWS IoT Core</div> | ||
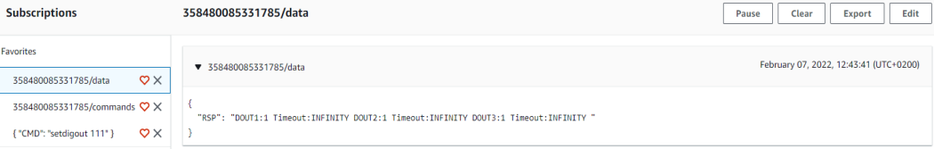
The response to the command will be shown in the Data topic: | The response to the command will be shown in the Data topic: | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | [[File:AWS_MQTT_17.png|frameless|alt=|center|934x425px]] | |
| − | < | + | <div style="text-align: center;">Figure 17. Response to a command in the data topic, the command was published in command topic</div> |
| − | |||
Revision as of 11:21, 17 March 2023
Setup your AWS account and Permissions
Refer to the online AWS documentation at Set up your AWS Account. Follow the steps outlined in the sections below to create your account and a user and get started:
NOTE – The examples in this document are intended only for dev environments. All devices in your production fleet must have credentials with privileges that authorize only intended actions on specific resources. The specific permission policies can vary for your use case. Identify the permission policies that best meet your business and security requirements. For more information, refer to Example policies and Security Best practices.
Create Resources in AWS IoT
Refer to the online AWS documentation at Create AWS IoT Resources. Follow the steps outlined in these sections to provision resources for your device:
NOTE – The examples in this document are intended only for dev environments. All devices in your production fleet must have credentials with privileges that authorize only intended actions on specific resources. The specific permission policies can vary for your use case. Identify the permission policies that best meet your business and security requirements. For more information, refer to Example policies and Security Best practices.
Provision the Device with credentials
Whole device, AWS IoT and testing information can be downloaded in PDF format here.
AWS IoT Core Configuration
Setting up AWS IoT Core
When logged in the AWS console, click on Services on the top left hand side screen, to access IoT core.
After accessing AWS IoT core, select Manage on the sidebar on the left side, then select Things (Manage- >Things). And click on Create things.
Afterwards for select Create single thing and click Next.
After creating single thing, enter Thing’s name and in the Device Shadow tab select Unnamed shadow (classic). Then click Next.
Then when selecting Device certificate, select Auto-generate a new certificate and click Next
After this select Create policy to create it and attach it to Certificate. In the Create Policy window, enter Policy name. In the Policy document (1) tab for Policy Action (2) select * and for Policy resource enter * .
After creating policy, return to Certificate tab (Seperate tab after pressing Create policy should‘ve popped out). Then select the created policy to attach it to the certificate and thing. After that click Create thing
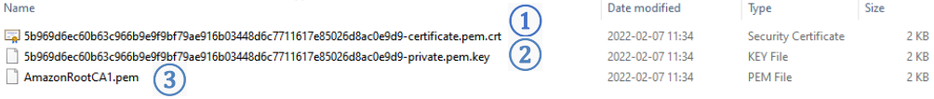
Then window with Certificate files and key files download options should pop out. It‘s recommended to download all files, because later some of them will not be available for download. The files that are required for usage with FMX devices are: Device certificate (1), private key(2), and Amazon Root CA 1 file(3), but it‘s recommended to download them all and store them in secured place.
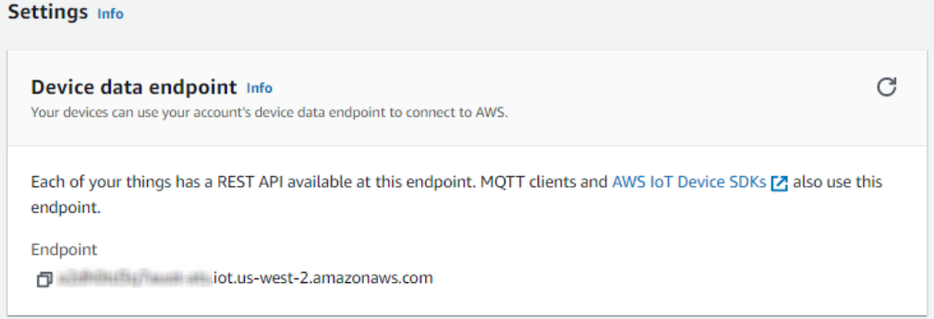
Finding device data endpoint (server domain)
To receive server domain (in AWS endpoint) click on the side bar on the left Settings. Or click on the side bar on left side Things, select the created thing, after it click Interact->View Settings. Whole path - (Things->*YourThingName*->Interact->ViewSettings). Page containing endpoint will open. Copy the whole endpoint address. Port for accessing this endpoint is 8883.
Configuring the device
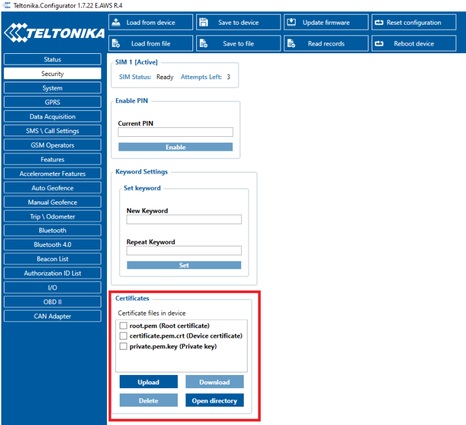
Security and certificates
Find Certificate file ending with extension pem.crt Private key file and AmazoonRootCA1 file (no need to change filenames). These file should have been downloaded when creating Thing in AWS IoT Core.
Upload the mentioned files in the Security tab in the Teltonika Configurator.
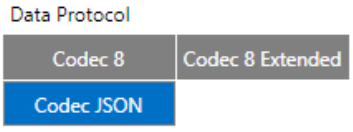
After uploading certificates, go to System tab and in Data protocol section select - Codec JSON.
Device GPRS configuration for AWS IoT Custom MQTT settings
In the GPRS tab, under Server Settings select:
- Domain – Endpoint from the AWS, Port: 8883
- Protocol – MQTT
- TLS Encryption – TLS/DTLS
In the MQTT Settings section select:
- MQTT Client Type – AWS IoT Custom
- Device ID – enter device IMEI (optional)
- Leave Data and Command Topics unchanged.
Save the configuration to the device.
Run the demo
The data received from the device can be found in the MQTT test client, which can be found in the bottom of sidebar on the left. To see incoming data, subscribe to topic - *DeviceImei*/data . Or subscribe to # to see all incoming outgoing data in the Topics.
Incoming data is received in JSON format, for e.g.:
To send SMS/GPRS commands to the device, in the same MQTT test client window select Publish to a topic. Enter topic name - *DeviceIMEI*/commands . In the Message payload enter wanted GPRS/SMS command in following format and press Publish:
The response to the command will be shown in the Data topic: